A hash table can only be added to another hash table 67. U 0 1 2 m-1 Earlier for a direct access table the size of the array T should be U the size of UHowever the hash table allows the size of the array to be m m U ie we can create an array of any size regardless of the size of.

Cryptomining Makes Noise Detecting Cryptojacking Via Machine Learning Sciencedirect
We call hx hash value of x.

Error in unique.default(x) hash table is full. HashTablehashTableint size A variable local to the constructor used here such vector object would be destroyed the moment this constructor call is finished. This Vista image should also contain some AppV virtual packages. This guide provides the Best AppLinked Codes in July 2021 for FirestickAndroid devices.
Hi The HASH value is used when using the Task. It is one part of a technique called hashing the other of which is a hash function. Hash Functions and Hash Tables A hash function h maps keys of a given type to integers in a xed interval 0N -1.
I had an issue recently whereby the hash value changed when ISO and WIM only were distributed out to the DPs The offender was the SCEP installed on the site server. The hash table should be an array with length about 13 times the maximum number of keys that will actually be in the table and Size of hash table array should be a prime number So let M the next prime larger than 13 times the number of keys you will want to store in the table and create the table as an array of length M. That did work for all the 6.
Begingroup Hash is not supposed to be unique. For this data an array would be the best choice. Hash Tables With Separate Chaining algs4csprincetonedu When we search or insert we first hash to find the list that could contain the key then sequentially search through that list.
Your computer is then more likely to get a wrong. The text was updated successfully but these errors were encountered. The needed packages have been sequenced and tested locally.
A hash table is not suitable for what you want to do. A Hash Table in CC Associative array is a data structure that maps keys to valuesThis uses a hash function to compute indexes for a key. This also comes into play when supplying a hash table to a cmdlet as an inputobject.
Hash Table is a data structure which stores data in an associative manner. Hello I am busy with building a new Vista image. Vector theLists size.
Sometimes we cannot predict in advance how many elements we will need to store in the hash table. If k is a key and m is the size of the hash table the hash function h is calculated as. I had exclusions set and still persisted.
If you _really_ want to use hash tables create an array of hash tables or create a hash table where the values are hash tables. Closed raandree opened this issue Jan 21 2019 9 comments. 7 5 075 0.
H k k mod m. A hash table also known as a hash map is a data structure that maps keys to values. Access of data becomes very fast if we know the index of the desired data.
Instead use the member variable vector and allocate the requested amount of lists. The next step was to install them with an advertisement to install the virtual applications. This is a popular alternative to FileLinked codes.
Copy link Owner gaelcolas commented Jan 21 2019 edited. One solution is to grow the hash table when the load factor becomes too large typically larger than 0. The first aspect I want talk about is piping a hash table to other cmdlets.
Some important notes about hash tables. You can add values to the hash table and remove values from the hash tables. If the load factor n m alpha dfracnm m n gets too large we are in danger of losing constant-time performance.
Based on the Hash Table index we can store the value at the appropriate location. To add the values to the hash table you need to use the below format. I created a dataset named state from the built-in matrix statex77 with two continuous variables Population and Income and two factor variables region and area.
Here we will look into different methods to find a good hash function. The hash function maps every key in the universal set U to a slot in the array TIf the size of the array T is m then. For example If the size of a hash table is 10 and k 112 then h k 112 mod 10 2.
When I change a configuration file in a 1 GB image sha1 and compressed size of it does not change. In a hash table data is stored in an array format where each data value has its own unique index value. Hash tables can also store the full hash codes of values which makes scanning down one bucket fast.
I hx x mod N is a hash function for integer keys I hxy 5 x 7 y mod N is a hash function for pairs of integers. As an example I will use the hash table created in yesterdays post Easily Create a PowerShell Hash Table. In fact if the hash code is long and the hash function is high-quality eg 64 bits of a properly constructed MD5 digest two keys with the same hash code are almost certainly the same value.
Data Structure and Algorithms - Hash Table. Image by author. However if I wanted to change a smaller image in a specific way to comply with the config file format that will work and produce the same hash there would not be a mathematically provable generic and fast as in faster than it should be.
A hash function is an algorithm that produces an index of where a value can be found or stored in the hash table.

Hash Digest An Overview Sciencedirect Topics
Https Openaccess Thecvf Com Content Cvprw 2020 Papers W48 Dang Fehash Full Entropy Hash For Face Template Protection Cvprw 2020 Paper Pdf

Bit Error Rate Guarantee For Quantum Key Distribution And Its Characteristics Compared To Leftover Hash Lemma
Https Openaccess Thecvf Com Content Cvprw 2020 Papers W48 Dang Fehash Full Entropy Hash For Face Template Protection Cvprw 2020 Paper Pdf

Biscotti A Blockchain System For Private And Secure Federated Learning

Hash Table Performance In R Part I R Bloggers

Hash Table Performance In R Part I R Bloggers
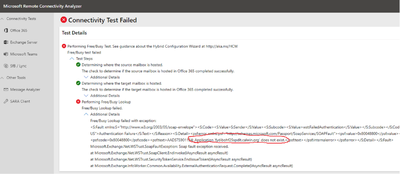
Demystifying Hybrid Free Busy Finding Errors And Troubleshooting Microsoft Tech Community

Mysql Error Key Specification Without A Key Length Stack Overflow
Call For Feature Supporting Of Expressions Issue 1091 Ropensci Plotly Github

Large Scale Integrative Taxonomy Lit Resolving The Data Conundrum For Dark Taxa Biorxiv

State Of The Art Structural Variant Calling What Went Conceptually Wrong And How To Fix It Biorxiv

Hash Digest An Overview Sciencedirect Topics

Hash Table Performance In R Part I R Bloggers

Hash Digest An Overview Sciencedirect Topics
Http Biorxiv Org Cgi Reprint 648683v2
Https Openaccess Thecvf Com Content Cvprw 2020 Papers W48 Dang Fehash Full Entropy Hash For Face Template Protection Cvprw 2020 Paper Pdf